The "Grey Market", where goods are traded through unofficial yet legal channels, offers enticing opportunities for buyers attracted by lower prices. But while perfectly legal, this market requires caution, or even all-out avoidance, particularly within the IT and Networking sector.
The promise of discounted IT equipment can be compelling, especially when you're shopping around for discounts on the big names, such as Cisco and HPE. However, when a discount seems too good to be true, it could be because it brings with it complexities surrounding compatibility, warranties, and support. There's a critical balance between cost savings and informed decision-making, but when it comes to IT, applying a healthy amount of due diligence is key, so you can ensure you're only purchasing equipment through authorised (and safe) channels. Let's take a look, then, at exactly what Grey Market IT is and what to look out for, so you can avoid buying dodgy kit that could land you in a tough spot.
What is Grey Market IT stock?

The grey market occupies a unique position in the world of commerce, nestled between the legality of official retail channels and the illegality of black markets. Unlike black markets, which deal in illicit goods or bypass legal channels altogether, the grey market legally redistributes products through channels that, while unofficial, are not inherently illegal. These goods can be genuine but are sold outside the manufacturer's authorised distribution networks. The differentiation from official retail channels lies in the absence of direct manufacturer endorsement and support, making the grey market a legitimate but complex part of global trade.
In IT, the grey market is particularly prevalent. It involves a wide variety of products, from laptops and smartphones to more specialised equipment such as network switches, routers, and wireless access points. These items, often integral to the infrastructure of businesses and individuals alike, find their way into the grey market through various channels, presenting an attractive alternative to official retail avenues due to their lower prices.
The sourcing of grey market items is diverse, spanning across international boundaries and often involving intricate supply chains. One common source is international purchases, where goods are bought in one country—sometimes benefiting from currency fluctuations, regional promotions, or lower local prices—and then sold in another without going through the manufacturer's authorised distributors. Another source is overstock sales, where excess inventory from a manufacturer or retailer is sold to third-party vendors. These vendors then offer the products at reduced prices, sidestepping the official retail channels.
Products can enter the grey market through liquidation sales, company closures, or even customer returns, further broadening the spectrum of how and where these items are sourced.
Understanding the grey market's nuances, especially within the IT sector, is crucial for countering companies who may be using the grey market to supply you. While it offers the allure of cost savings, it also demands a heightened awareness of the potential risks associated with purchasing outside official channels, such as issues with warranties, support, and product authenticity. When you're gathering quotes, if your pricing is simply too good to be true, this could be a big red flag.
Where Does "Grey Stock" Come From?
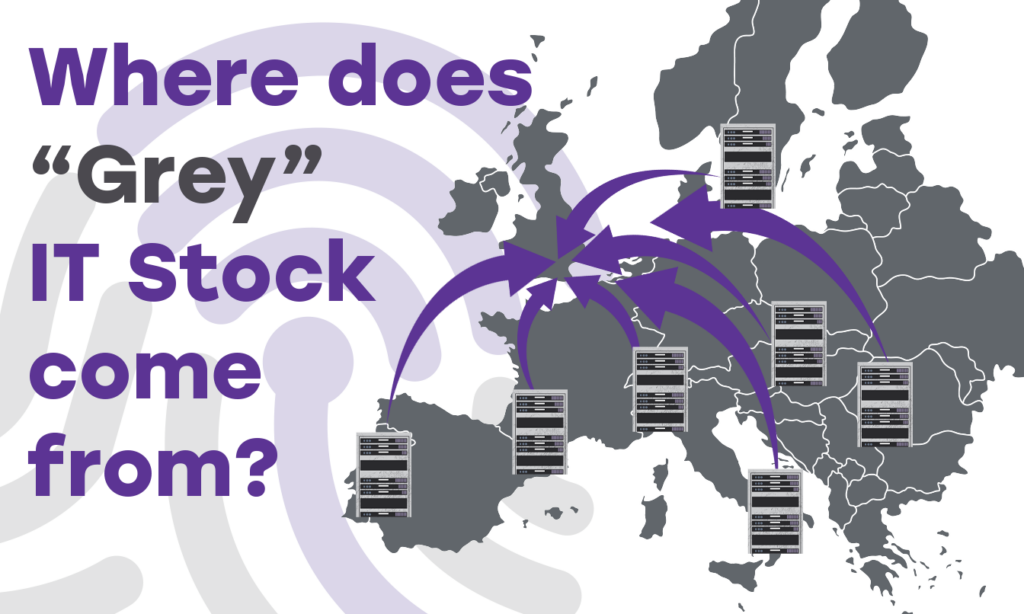
The grey market in IT equipment flourishes on the fringes of official supply chains, operating through a global network that sources and distributes products outside the authorised channels of manufacturers. Grey market IT products, such as discounted Cisco Meraki switches, find their way into the hands of consumers and businesses, through various global mechanisms, underscoring the truly international nature of these transactions.
Acquiring Grey Market IT Products
A common scenario involves IT resellers acquiring products like big-name networks switches, access points, and routers at steep discounts, often raising eyebrows about the origins of such deals. These products may not always come through the direct supply lines established by manufacturers.
Instead, they are sourced through a variety of unofficial channels that bypass traditional distribution networks. For example, an IT supplier not recognised as a Cisco partner might offer Cisco Meraki switches at prices significantly lower than market rates. This situation typically indicates that the products have been sourced from outside the usual vendor-approved channels.
The Global Grey Market
The grey market's reach is undeniably global, with products moving across borders in ways that blur the lines of official distribution. Items can originate from virtually anywhere in the world, making their way through a complex web of buyers, sellers, and intermediaries before reaching the end user. A vivid illustration of this is the resale of over-ordered IT equipment, such as a European hospital offloading excess Cisco Meraki switches. These products, originally purchased in bulk to secure a discount or due to procurement overestimates, become surplus to requirements and are sold into the grey market to recoup expenses.
Such practices underscore the grey market's adaptive and opportunistic nature, capitalising on the discrepancies between supply and demand across different regions. The lack of a single point of origin for grey market goods complicates efforts to regulate or monitor these transactions, as products can be sourced from overstock situations, liquidation sales, or even other grey market transactions, creating a self-sustaining cycle of distribution that operates parallel to, yet distinctly apart from, official supply chains.
Understanding the origins and sources of grey market IT equipment is crucial for buyers navigating this space. It highlights the importance of diligence and the need to weigh the benefits of lower prices against the potential risks and uncertainties associated with these products. This global marketplace, while offering opportunities for savings, also demands a careful consideration of the implications for warranty, support, and overall product authenticity.
The Risks of Grey Market Products

While the grey market offers cost savings on IT equipment, it comes with a spectrum of risks that buyers must be aware of. The appeal of lower prices can often obscure the potential pitfalls associated with these purchases, including compatibility issues, warranty and support challenges, and the risk of counterfeit products. Understanding these risks is essential for making informed decisions and mitigating potential problems down the line.
Compatibility Issues
One of the immediate concerns when purchasing grey market IT equipment is compatibility. Products intended for different geographical markets may come with incompatible power cables or require adapters that are not readily available or that may compromise device performance. Hardware and software configurations might differ from region to region, leading to potential incompatibilities with existing systems. Network switches and access points acquired through the grey market may not operate seamlessly with the buyer’s existing setup, leading to unexpected costs and complexities in achieving a functional network infrastructure.
Warranty and Support Challenges
Another significant risk involves warranties and support services. Manufacturers often stipulate that warranties and support agreements are only valid if the product is purchased through authorised channels. This means that grey market purchases may not be eligible for manufacturer support or warranty claims, leaving buyers with limited recourse if the equipment fails or requires servicing. The process of registering a product for warranty or support typically requires proof of purchase from an authorised reseller, and discrepancies can easily reveal the grey market origin of a product, resulting in denied service claims.
Risk of Counterfeit Products
Perhaps the most concerning risk associated with the grey market is the potential for encountering counterfeit products. The lack of transparency and official oversight in grey market transactions creates an environment ripe for the distribution of counterfeit, substandard, or misrepresented items. These products may bear a close resemblance to genuine items but often fall short in terms of performance, reliability, and safety. The consequences of integrating counterfeit IT equipment into a network can be severe, ranging from operational failures to security vulnerabilities.
While the grey market can offer attractive pricing for IT equipment, the associated risks demand careful consideration. Compatibility issues, warranty and support challenges, and the potential for encountering counterfeit products are significant factors that can undermine the initial cost savings, potentially leading to higher total costs and operational disruptions.
Identifying Grey Market Products
The ability to identify grey market products before purchase is essential for avoiding the pitfalls discussed earlier. Fortunately, there are a variety of methods of identifying these items, so you can carry out your due diligence before and after purchasing from suppliers.
Price Checks
One of the most glaring indicators of a grey market product is its price. If an offer for IT equipment, such as switches, routers, or access points, comes in significantly lower than the market rate or the manufacturer's suggested retail price (MSRP), it warrants a closer look. While there are legitimate deals and discounts to be had, especially during sales events or from overstock, drastic price discrepancies often signal grey market origins. Conducting thorough price comparisons across multiple reputable vendors can help establish a baseline for what constitutes a reasonable discount versus a grey market red flag.
Vendor Verification
The legitimacy of the vendor is another critical factor in identifying grey market products. Authorised resellers and partners are typically listed on manufacturers' websites, providing a straightforward way to verify if a seller is operating within the official distribution network. Buyers should be wary of vendors that:
- Lack a physical address
- Offer limited contact information
- Display a history of selling a wide array of unrelated products
These characteristics can indicate a seller's potential involvement in the grey market. Engaging directly with manufacturers or authorised distributors for purchase recommendations is also a proactive step in ensuring product authenticity.
Too-Good-To-Be-True Offers
Deals that seem too good to be true often are, especially in the context of high-value IT equipment. Skepticism should be applied to offers that significantly undercut competitors on price without a clear rationale, such as clearance sales or official promotions. Additional red flags include vague product descriptions, the absence of warranty information, or the use of stock images instead of actual photos of the item being sold. Potential buyers should request detailed product information, including serial numbers, which can often be checked against manufacturer databases to verify authenticity and warranty eligibility.
Conducting Checks on Current Equipment
For businesses and individuals who have already purchased IT equipment, conducting periodic checks on current infrastructure is advisable. This can involve verifying serial numbers with manufacturers, assessing warranty status, and ensuring that all devices are receiving updates and support as expected. Identifying grey market items within existing setups allows for corrective measures to be taken, such as seeking out reputable sources for future purchases or upgrading non-compliant equipment to mitigate risks.
Identifying grey market products is a crucial skill in safeguarding IT investments and maintaining operational integrity. By applying rigorous price checks, verifying vendor credentials, scrutinising offers, and conducting regular equipment audits, buyers can significantly reduce the risks associated with grey market transactions.
Protecting Yourself from the Grey Market
In IT procurement, safeguarding against the pitfalls of the grey market is paramount for maintaining the integrity, security, and performance of your technological infrastructure. This section offers guidance on verifying the legitimacy of quotes and products, highlighting the indispensable role of trusted IT providers and the value of forging strong partnerships with official vendors. By emphasising the significance of engaging with reputable partners and suppliers, we aim to arm you with strategies to ensure product authenticity and comprehensive support.
Verifying the Legitimacy of Quotes and Products
- Request Detailed Documentation: Always ask for detailed product descriptions, official documentation, and proof of authenticity when receiving quotes. Legitimate vendors will be able to provide serial numbers, warranty information, and direct assurances from the manufacturers.
- Utilise Manufacturer Verification Tools: Many manufacturers offer online tools or customer service lines that allow you to verify product serial numbers and warranty status. Utilise these resources to confirm the legitimacy of the products you're considering.
- Seek Transparency: Reputable vendors should be transparent about the source of their products. Don't hesitate to ask direct questions about where and how they source their IT equipment. Genuine partners will have no issue disclosing this information.
The Role of Trusted IT Providers and Partnerships
- Engage with Authorised Resellers: Purchasing from authorised resellers or directly from the manufacturers is one of the most effective ways to avoid grey market pitfalls. These entities are held to high standards by the manufacturers and are regularly audited to ensure compliance with quality and service benchmarks.
- Build Long-Term Relationships: Developing long-term relationships with trusted IT providers offers numerous benefits, including reliability, consistency in quality, and access to expedited support. These providers have a vested interest in maintaining their reputation and will go the extra mile to ensure your satisfaction.
- Leverage Vendor Partnerships: Trusted IT providers with established relationships with official vendors can offer invaluable insights and access to exclusive deals, promotions, and updates. Their expertise can guide you through the complexities of IT procurement, ensuring you receive products that are fully supported and compliant with manufacturer standards.
Importance of Reputable Partners and Suppliers
Working with reputable partners and suppliers is crucial for navigating the IT procurement landscape successfully. These entities not only guarantee the authenticity of the products they sell but also provide comprehensive after-sales support, warranty services, and advice. In an industry where technological compatibility, security, and reliability are non-negotiable, the value of establishing a network of trustworthy suppliers cannot be overstated.
- Conduct Due Diligence: Research potential suppliers thoroughly, looking for reviews, testimonials, and case studies. A strong track record of delivering quality IT solutions is a good indicator of a supplier's reliability.
- Assess Support Capabilities: Before committing to a purchase, evaluate the supplier's support infrastructure. Reliable vendors offer robust after-sales support, including technical assistance, warranty claims processing, and maintenance services.
By sticking to these guidelines and prioritising relationships with reputable IT providers and official vendors, organisations can significantly mitigate the risks associated with the grey market. Protecting your IT investments begins with informed decision-making, diligence in vendor selection, and a commitment to quality and authenticity.
Opt for Authorised Partners

Opting for authorised resellers and partners when purchasing IT equipment is a decision that offers numerous benefits, from enhanced warranty protection to assured product authenticity.
Warranty Protection
One of the most significant advantages of purchasing through authorised partners is the comprehensive warranty protection that accompanies genuine products. Manufacturers often limit warranty services to items bought from their network of approved sellers, ensuring that any defects or issues are promptly addressed without additional cost. This warranty protection is not just about fixing problems; it's a testament to the product's quality and the manufacturer's commitment to their customers' satisfaction.
Support and Assistance
Authorised resellers and partners have direct access to the manufacturers' resources, including detailed product knowledge, technical support, and advanced training. This direct line not only facilitates a smoother, more efficient resolution of any technical issues but also provides valuable guidance for integrating new technology into existing systems. The level of support available through authorised channels significantly surpasses what might be found in the grey market, where the provenance of products can complicate or nullify support claims.
Peace of Mind and Product Authenticity
Purchasing from authorised sources offers an unmatched level of peace of mind. Buyers can be confident in the authenticity of their products, secure in the knowledge that they are compliant with all relevant regulations and standards. This assurance extends to software licenses, updates, and patches, all of which are crucial for maintaining the security and functionality of IT systems. The risk of counterfeit or tampered products is virtually eliminated, protecting your investment and your network's integrity.
The Value of Established Relationships
Building a relationship with a trusted vendor is invaluable. Over time, these partnerships can yield benefits beyond individual transactions, including access to expert advice, customised solutions, and early notifications of new products and innovations. Authorised partners understand your business and its technological needs, enabling them to anticipate requirements and offer solutions that align with your strategic goals.