In today's digital age, technology has become a vital part of education. From online classes to digital assessments, technology has revolutionised the way students learn, and educators teach. However, with the increasing use of technology in education comes the need for stronger cyber security in education settings. Cyber-attacks can compromise sensitive information, disrupt online learning, and cause irreparable damage to an institution's reputation. In this article, we'll cover why education is a target and what to look out for.

Why is cyber security in education important in 2023?
Most people are aware of the dangers posed by cyber attacks to businesses and individuals, but have you ever considered the impact cyber criminals could have on an educational institution? Cyber attacks can not only compromise the privacy and data of an institution, but also the safety and security of teachers and students alike.
In today’s age of remote working, schools, colleges, and universities are also leaning into the world of hybrid learning environments, where students regularly join online classes and submit coursework, and teachers keep records of their student’s progress.
With this comes risk; in a recent audit more than 600 schools (out of the 800 that responded) recorded that they had experienced at least one type of cyber-attack, including ransomware and phishing attacks. With students connecting to various networks using various devices, the opportunity for a data breach is extremely high without the right cybersecurity measures in place.
4 common cyber-attacks to look out for
There are 4 common cyber-attacks that are used to target education. We’ve summarised them below so that you can learn the reasons why they are used specifically to target schools and universities.
DDoS Attacks
A Distributed Denial of Service (DDoS) attack is a malicious act wherein a cybercriminal attempts to disrupt the normal functioning of a server, service, or network by overwhelming it with internet traffic. It is one of the most common online attacks that can cripple websites and interrupt internal services for extended periods of time.
In effect, DDoS attackers are using multiple compromised systems to target a single system. This creates massive amounts of data being sent to the targeted server or network to overwhelm the resources and prevent legitimate users from accessing the services they provide. The goal is to deny access and cause disruption while consuming bandwidth, resources, and other computing power on the targeted system. By doing this, attackers can severely reduce performance and sometimes shut down an institution’s systems and websites altogether.
This can be an easy method of attack for an experienced cyber criminal when the network and systems are poorly protected. We’ve also seen attacks carried out by students and teachers for reasons including wanting an extra day off, to being upset about the way in which a complaint was handled.
Phishing
The most common and least sophisticated method of cyber-attack, but one that can open up a route straight into an institution’s systems and storage spaces. They are often disguised as harmless emails sent to a large number of peers within the organisation, however, these emails are masked to look like legitimate login pages for your productivity and billing tools but are actually stealing your login credentials. These credentials are then used to access the legitimate systems within your technology structure, at which point cyber criminals can gain private data and information.

The main aim of a phishing attack is data theft and is used to target all levels of education, because all schools and universities store their student and teacher data, including sensitive information such as names, addresses and contact details. Information like this can be valuable to cybercriminals for a number of reasons, including whereby they sell the data for financial gain or use it as a method of gaining a ransom in return for the safe return of the data.
The main concern around phishing attacks is that your IT staff and cyber security tools may not be aware of a successful phishing attack until long after it has taken place, meaning attackers may have had access to sensitive data for any length of time. If you want to learn more about phishing attacks check out our recent article here.
Financial Gain & Ransomware
You may be wondering how criminals can make financial gain from schools, but when you consider private schools and universities, where large sums of money are received, you can begin to see why these institutions become high-value targets for cyber-attacks.
There are a number of ways in which these finances can be extorted by cybercriminals. Universities and private schools will often have online portals for the transaction of fees. These portals can be targeted if not protected appropriately by the institution, giving criminals the chance to re-route transactions or simply gain access to your financial data.
The second method of attack is a fairly recent type of attack. Ransomware is a type of malicious software that threatens to publish the institution’s data or block access to their files unless a ransom is paid. It is one of the most serious cyber threats facing businesses, education and individuals today, as it can have devastating financial and reputational consequences.
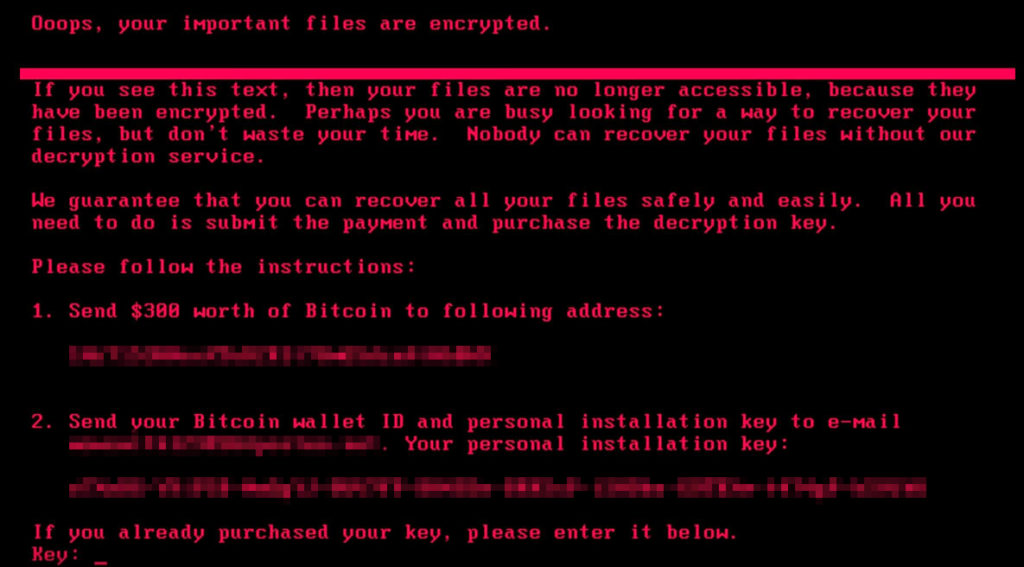
Ransomware attacks typically begin when the victim opens an infected attachment or clicks on a malicious link in an email, instant message, or website. The attack then infiltrates the victim’s system and locks them out by encrypting their valuable files with strong encryption algorithms that are nearly impossible to break without the encryption key held by the attackers. Victims are then presented with a demand for payment in exchange for the decryption of their data or access to their system.
Espionage
No, this isn’t a Bond film, but higher education institutions can often hold valuable intellectual property as they can also be research centres.
Institutions that specialise in science, engineering, and medical research have been targeted in the UK previously, and due to the fact that they often hold data that can impact governments, these types of attacks are often backed and funded by international governments, so must be taken extremely seriously.
How can education protect against cyber-attacks?
The UK government regularly updates their guidance on how educational institutions should protect against cyber criminals. These methods should be part of any comprehensive cyber security plan, which you can read more about here. Your IT team should consider this when planning out your protection methods.
According to the UK government, institutions should carry out the following:
- Protect every device on every network, using a properly configured boundary or software firewall.
- All devices used to provide network access around campuses should be known and recorded, with each having their security features enabled, configured and regularly updated.
- User accounts should only be given access to perform the actions and role required and should be authenticated before being allowed access to data and systems.
- Accounts should be protected using multi-factor authentication.
- Install and maintain up to date anti-malware and anti-virus software across devices and networks, including cloud-based networks.
- Administrators should regularly check the security of software installed across networks.
- All software and devices connected to a network should be licensed for use and regularly updated/patched with security updates.
- Data should be backed up to at least 3 locations, on at least 2 different devices, with 1 being off-site.
- Your continuity and disaster recovery plan should include regularly tested contingencies in response to cyber-attacks.
- Serious attacks should be reported.
- You must conduct a Data Protection Impact Assessment by statute for personal data you hold required by GDPR.
- All staff with access to educational IT networks must be trained in the basics of cyber security.
Conclusion
In conclusion, cybersecurity in education is essential for the success of both students and institutions. It provides a safe space for students to learn and research while protecting sensitive data and records of an institution.
With responsible implementation of cyber security measures, students can trust their educational environment to be secure. Teachers should make themselves aware of the latest cybersecurity trends and equip themselves with the knowledge they need to educate their students on the importance of these measures.
You can always contact Haptic Networks if you require assistance with your school or university’s cyber security or technology by clicking here and getting in touch.